We’ve performed multiple cybersecurity assessments over the past two years, across two industry sectors: DoD engineering contracting (DFARS / NIST 800-171) and healthcare (HIPAA Security Rule). We’ve gleaned a lot of data about small business cybersecurity from these assessments. I’m writing this blog to expound upon the biggest weakness we’ve seen these businesses exhibit: being able to detect a cyber-attack.
Types of Cybersecurity Controls
There are four types of cybersecurity “controls”, aka safeguards, and implementing a mix of these controls is required for a robust defense-in-depth-based cybersecurity program. Here are the four control types, with some examples of each:
- Avertive: Warning banners, honeypots, acceptable use policy, user training
- Preventive: Access control enforcement, encryption, strong (multifactor) authentication, patching, application whitelisting
- Detective: Audit trails, intrusion detection systems, checksums, honeypots
- Corrective: Incident Response/Contingency/Disaster Recovery plans, backup restore procedures, redundancy
The graphic below shows how these control types are related to each other and to the threat-vulnerability-impact risk chain:
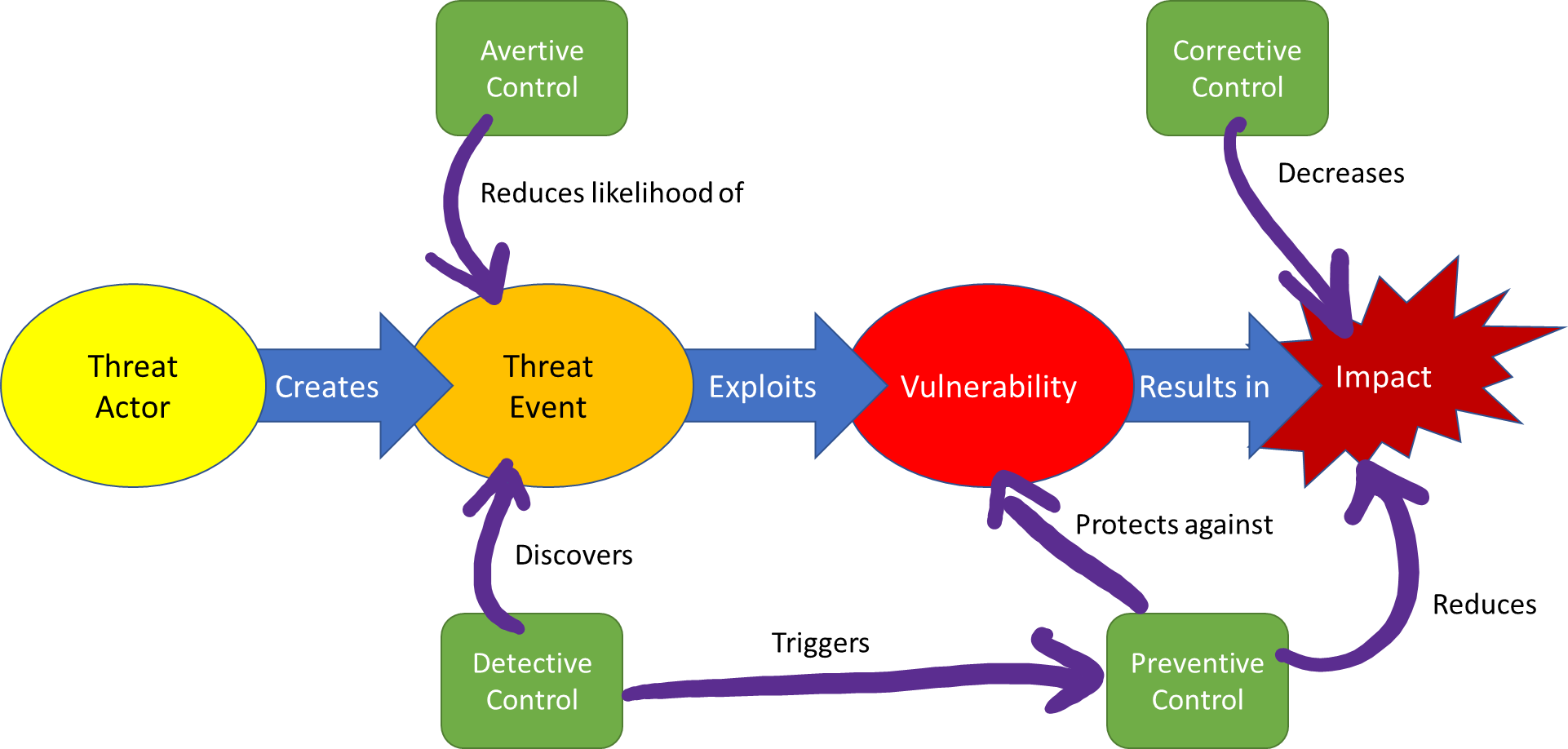
Lack of Detective Cybersecurity Controls for Small Businesses
Of these four control types, the businesses we’ve assisted with assessing their cybersecurity program are overwhelmingly deficient in detective controls. This shouldn’t be a surprise to any cybersecurity professional, and doesn’t surprise me. Detective controls can be difficult to implement, especially the auditing (logging) of system components and monitoring those audit reports. We’ll talk about some simple detection tactics in a bit, that (especially) small businesses can quickly implement. What was surprising to me was that most of these organizations have at least the awareness that social engineering—in the form of phishing—is a huge threat, and that many have some strategy in place to counter that threat. The cybersecurity community is doing a good job of drawing awareness to this threat. Many of the organizations have phishing training and awareness in place, to include phishing simulation campaigns, which train users to spot phishing attempts. So, these organizations have some detective controls in place for social engineering, which is the single biggest threat to any organization. This is good news.
That being said, these organizations were deficient in detective controls relative to the other three control types at average ratios from 1:2 up to 1:4. Below is a representative example Threat Event Control Matrix for an organization we assisted through a Risk Assessment using our Assumed Risk approach:
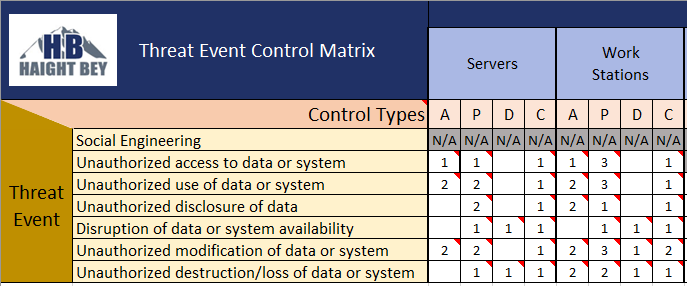
The “A”, “P”, “D”, “C” columns under the Servers and Work Stations asset classes represent numbers of controls of each type. You can see this organization has far fewer Detective (“D”) controls in place compared to the other types.
What has been surprising to these organizations is that adding Detective controls can be simpler than they think. While a robust component audit logging and Security Information and Event Management (SIEM) implementation and monitoring solution will be a challenge for the average small business, there is plenty of low-hanging detective fruit they can pluck.
What are easy ways to implement Detective Cybersecurity Controls?
- Perform a periodic network component and service scan, using Nmap or an equivalent free tool, and compare these scans, daily if possible—this will help detect new or changed assets on the network and potentially discover rogue or unauthorized devices. Doing so will help your organization meet a top four priority security control from both CIS and the ASD: maintain a hardware and software asset list. Remember, “if you don’t know what’s on your network, you don’t know where your vulnerabilities are”.
- Perform vulnerability scans on common components, such as workstations and servers, and use the results of these scans to inform your organizational operating system and software patching strategy. There are free and low-cost vulnerability scanners, such as Microsoft Security Compliance Toolkit for Windows workstations and servers, and Tenable Nessus® for really any component. An adequate patching strategy meets another top four security control.
- Be on the lookout for unauthorized use of administrative privileges. If your organization doesn’t have the resources to man a SIEM implementation, at least query the domain controller periodically for administrative logons in the domain. While you’re at it, you can meet another top four control by following the principle of “least privilege” and reducing the assignment of administrative privileges to only those accounts that absolutely need it.
Another strategy is to “seed” the Active Directory with some fake, disabled, “honeytoken” accounts. Honeytokens are enticingly named but fake accounts (what adversary could resist an account named “OrgADadmin”), designed to lure the adversary into attempting to use them on your network. Then your organization can monitor for any use of the honeytoken on the network and hone in on the target components for further investigation.
If you want to learn more about the current DFARS/NIST 800-171/CMMC landscape, or how you can build a CMMC-compliant cybersecurity program, grab a seat in one of our Workshops. Or, drop us a line; we love talking about all this stuff!
Good Hunting!
–Adam Austin
Cybersecurity Lead
Updated 5/25/2022



