What was the main project during my Cybersecurity Technician internship?
During my internship from June to August 2017, my main project for Haight Bey & Associates LLC (HB&A) was to configure a free network-monitoring tool to monitor for an array of network traffic anomalies. This tool was LogRhythm’s Netmon Freemium and it allows users to create dashboards and graphical visualizations powered by the Kibana GUI plugin. My mentor utilized a resource from the SANS Institute which displayed a concise list of 11 network traffic anomalies. This resource is available here for download with a registered SANS account. Essentially, this served as a practical guide for developing the visualizations and dashboards in LogRhythm Netmon Freemium. My mentor and I successfully implemented several dashboards but some required the creation of Deep Packet Analysis Rules (DPAs) through the built-in Lua scripting engine for analyzing custom metadata.
What Lua software did I write for LogRhythm NetMon Freemium?
DPAs that I implemented include:
- Parse_DNS_Query – a parsing algorithm that takes the ‘Query’ field and outputs the second-level domain representation e.g. “abc.com”, “abc.co.uk”
- Find_New_Obs_Doms – a search algorithm for finding a second-domain domain in an array of previously queried domains and outputs true if it was discovered
- Get_Reg_Date – a parsing algorithm that caches the WHOIS information of a second-level domain and returns the date when it was registered
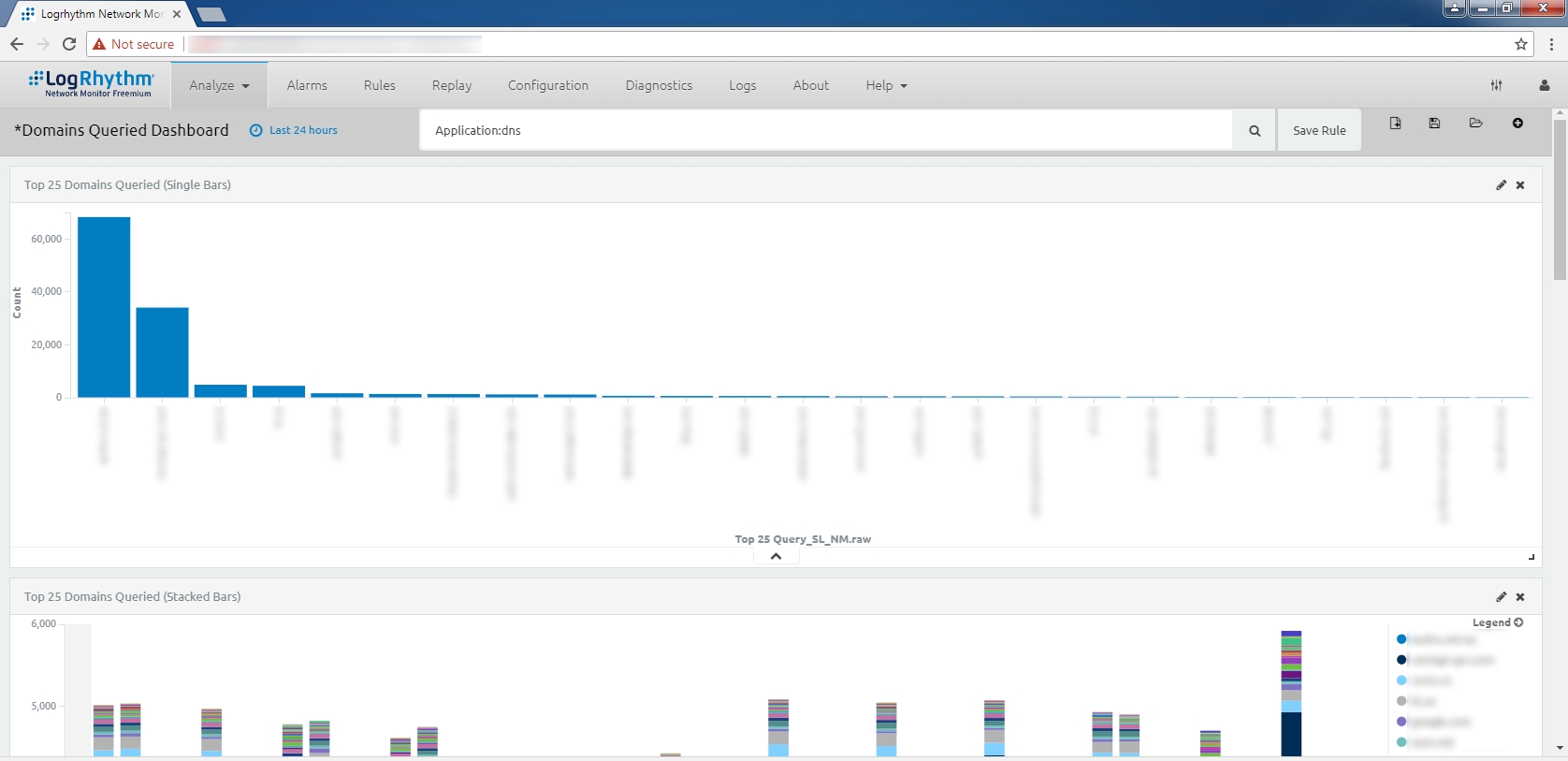
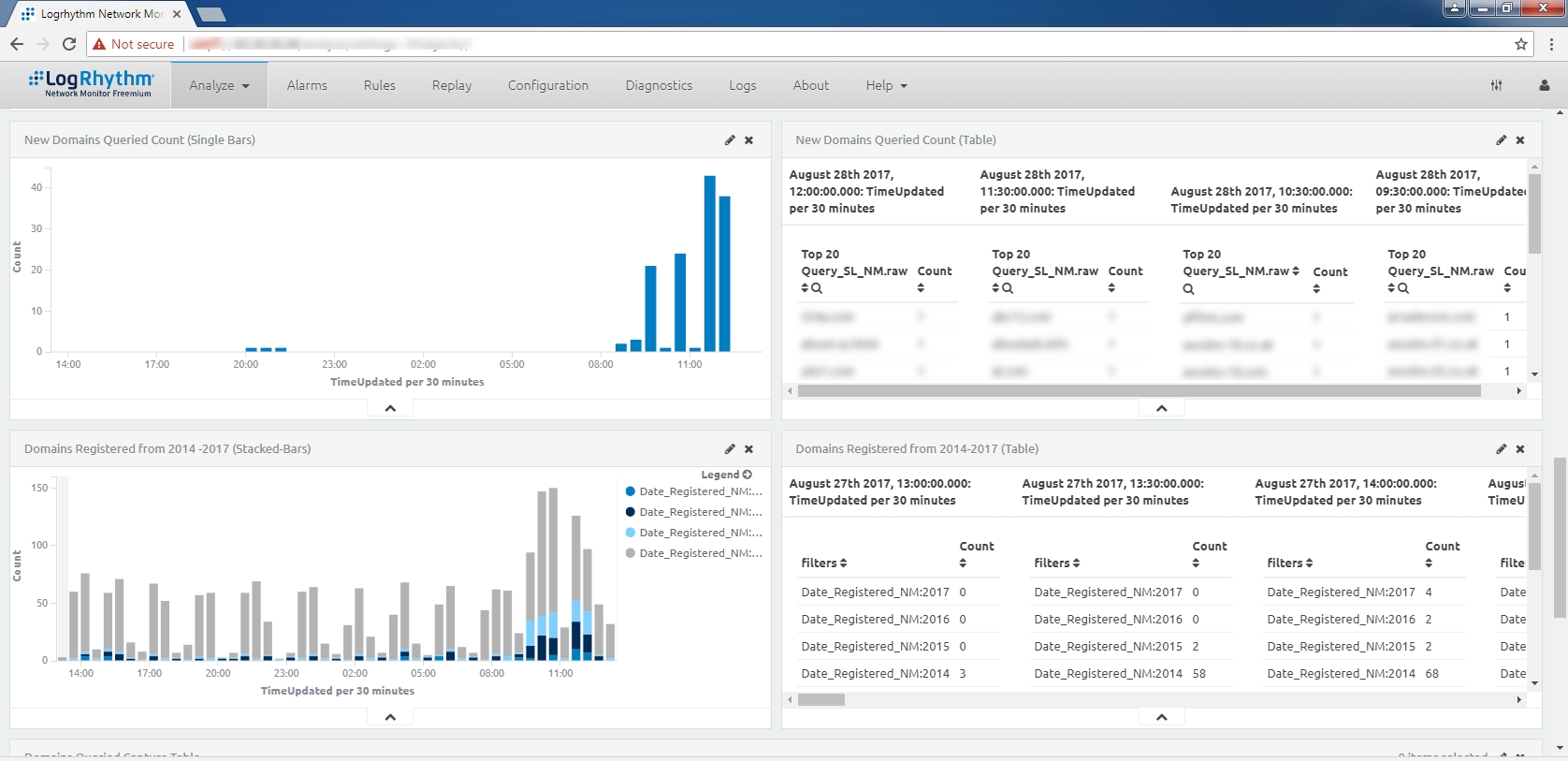
These DPAs were used to create dashboards to monitor the “Top DNS Domains Queried” and “Newly Observed/Newly-Registered Domains” standards presented in the SANS resource. We then created a single dashboard to encapsulate all of this information. Our goal was to display such information concisely so that a “Hunter” i.e. network security analyst could use the dashboard to better narrow down queried domains that would require further investigation. Below are screen captures of this dashboard which displays:
- The top 25 second-level domains queried relative to selected time-frame
- The top 25 second-level domains queried with respect to the time of occurrence
- The number of second-level domains queried for the first time
- The number of second-level domains registered during 2014, 2015, 2016, and 2017
Why is DNS monitoring important?
Monitoring this DNS information is crucial for any type of business because it helps the “Hunter” find second-level domains that could suggest malicious activity. This includes:
- Second-Level domains from foreign adversaries or that are misspelled (g00gl3.com)
- Second-Level domains queried for the first time during closed hours
- Second-Level domains registered during a recent day, week, month, or year
According to the SANS resource, these anomalies may suggest new phishing campaigns, new or highly targeting operations and other malicious activity. Hence, this dashboard can help empower the “Hunter” when he/she performs daily analysis on DNS traffic.
Submitting our Lua software and Kibana dashboards for LogRhythm's "Rule Your Network Challenge"
We submitted our DNS anomaly monitoring solution to LogRhythm’s Network Monitor Rule Your Network Challenge. This competition encouraged individuals from any background to submit their custom visualizations and dashboards for the chance to win different prizes. There were three categories participants could submit their work toward:
- Novel Threat Detection
- Best Security Hunting Dashboard or Use Case
- Best IT Operations Use Case
In September 2017, the judges at LogRhythm informed us that our entry had won the second category! This is what they had to say about our submitted visualizations and dashboard:
“HB&A, in [their] winning entry, created custom DPA rules that enriched DPA traffic by looking up the host name and adding in “whois” information, including how long the domain had been registered. Combining this enrichment rule with a new dashboard led to a hunting dashboard that maps nicely to SANS best practices. Using the rule and dashboard combination, it is trivially easy to identify new domains that haven’t been seen before, recently created domains, and other indicators that provide a rich hunting environment!”
Developing Free Cybersecurity Solutions for Small Businesses
I am very proud of this achievement because this demonstrates HB&A’s expertise and knowledge in configuration management. This dashboard was a component of a much larger project that focused on creating a network monitoring solution that is economically viable and practical for small/mid-sized businesses. In fact, my mentor and I wrote a blog and white paper that further elaborates on the project-cycle as well as our evaluation of LogRhythm Netmon Freemium. I felt very fortunate and privileged to work on this project because it served as a fantastic opportunity to test my software development and algorithm design skills. I will be working with HB&A to continue developing new visualizations and dashboards within LogRhythm Netmon Freemium.
–Jim Lee
Cybersecurity Technician



